Our Magnificent Blogs
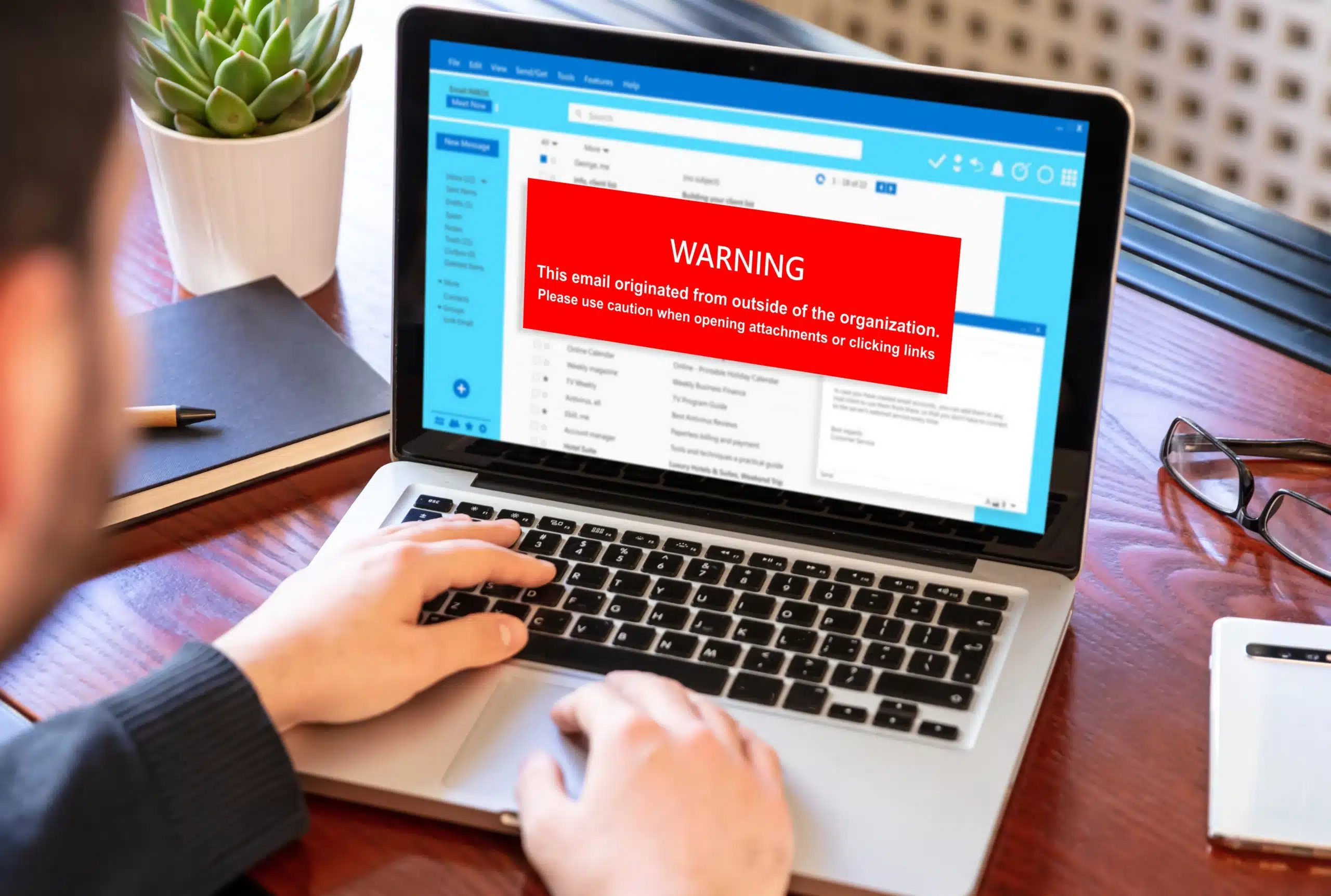
Don’t Get Hooked: Spear-phishing Risks
Phishing scams are nothing new, but today’s most dangerous cyberthreats go far beyond poorly written emails asking for your bank account number. One of the most sophisticated and costly types of phishing today is spear-phishing, a targeted attack that impersonates someone you know or trust to trick you into giving up sensitive data or access.…
Are You Compliant with E-Waste Laws?
Electronic waste (or e-waste) is one of the fastest-growing waste streams in the world. As companies upgrade their IT equipment, old devices pile up, and what happens next isn’t just an environmental concern, it’s a legal one. Many businesses don’t realize that improper disposal of electronics can lead to hefty fines and reputational damage. In…
AI and HIPAA: Risks and How to Stay Compliant
Artificial Intelligence (AI) has reshaped how we work, and healthcare is no exception. From chatbots assisting patients to predictive tools enhancing diagnostics, AI offers time-saving and accuracy-boosting benefits. But when sensitive health information is involved, so are strict regulations, especially those under the Health Insurance Portability and Accountability Act (HIPAA). While AI tools can improve…
Continue Reading AI and HIPAA: Risks and How to Stay Compliant
Your Old Devices Are a Data Breach Risk
As businesses and individuals upgrade their tech, old electronics pile up fast. But before you toss out that outdated laptop or broken smartphone, ask yourself: What’s still stored on that device? Every year, millions of data-rich devices are discarded improperly, putting personal and corporate data at risk of exposure. Whether you’re an IT manager at…
How to Prevent Downtime That Hurts Your Business
When your business’s technology goes dark, everything else grinds to a halt. Emails stop, sales are lost, customer service drops, and employee productivity plummets. It’s not just a momentary inconvenience. Downtime is a silent killer of business growth. If you’re a small business owner or IT manager, avoiding downtime should be at the top of…
Continue Reading How to Prevent Downtime That Hurts Your Business
10 Smart Ways to Use AI in Your Business Strategy
Artificial intelligence (AI) has moved beyond the realm of science fiction and experimental labs, it’s now a core driver of innovation and growth for businesses of all sizes. Whether you’re managing a startup, running an SMB, or scaling a larger enterprise, integrating AI into your daily operations can enhance productivity, boost efficiency, and improve customer…
Continue Reading 10 Smart Ways to Use AI in Your Business Strategy
Hybrid Cloud vs. Full Migration: How to Choose the Right Strategy
As businesses accelerate their digital transformation efforts, cloud adoption has become a top priority. Organizations are moving away from on-premises data centers in favor of more agile, scalable, and cost-effective cloud solutions. However, one crucial decision remains: Should you go for a hybrid cloud approach, combining on-premises and cloud infrastructure? Or should you fully migrate…
Continue Reading Hybrid Cloud vs. Full Migration: How to Choose the Right Strategy
Why Dual Internet Services Are Essential for Modern Businesses
In today’s fast-paced business world, reliable internet is a must. From processing transactions and handling customer inquiries to supporting remote work and running cloud applications, businesses rely on stable connectivity to keep operations moving smoothly. Unfortunately, outages happen, often at the most inconvenient times. The recent Metronet outage in Iowa is a reminder of the…
Continue Reading Why Dual Internet Services Are Essential for Modern Businesses
World Mental Health Day: Navigating Technology and Work-Life Balance
The Intersection of Technology and Mental Health As World Mental Health Day approaches, it’s time to reflect on how technology impacts our mental well-being, particularly when it comes to maintaining a healthy work-life balance. Technology is now deeply embedded in both our professional and personal lives, and while it brings countless benefits—such as increased productivity,…
Continue Reading World Mental Health Day: Navigating Technology and Work-Life Balance
Why the Break/Fix Approach is Hurting Your Business
For years, many businesses have relied on a break/fix approach to managing their IT needs. The premise is simple: when something breaks, you fix it. This method, often seen as cost-effective and straightforward, might seem like a solid option for businesses looking to avoid high, ongoing IT service costs. However, the break/fix approach is no…
Continue Reading Why the Break/Fix Approach is Hurting Your Business
Here’s How You Can Recycle Your E-waste
E-waste is a significant environmental concern, with millions of tons of discarded electronics piling up in landfills each year. These devices contain hazardous materials like lead, mercury, and cadmium, which can leach into the soil and water, causing severe environmental damage and posing health risks to communities. But there’s a better way to deal with…
Why is Staying HIPAA Compliant Crucial for Medical Businesses?
Ensuring HIPAA compliance is crucial for medical businesses to protect patient privacy, avoid penalties, and maintain trust. Implementing robust security measures, regular risk assessments, and employee training can help healthcare organizations enhance their security posture and ensure compliance. Discover how Dymin can help your medical business stay HIPAA compliant.
Continue Reading Why is Staying HIPAA Compliant Crucial for Medical Businesses?
The Secrets MSPs Don’t Want You to Know
In today’s fast-paced business world, Managed Service Providers (MSPs) play a crucial role in maintaining the IT infrastructure of companies. These service providers promise to streamline your operations, enhance security, and keep your technology running smoothly. However, not all MSPs are created equal, and there are certain industry secrets they might not want you to…
How to Use AI Responsibly in Your Business
Artificial Intelligence (AI) has transformed the way businesses operate, offering powerful tools to enhance efficiency, drive innovation, and improve customer experiences. However, the integration of AI into business processes must be handled responsibly to ensure ethical use, compliance with regulations, and the protection of sensitive data. In this blog post, we will explore how businesses…
The Importance of Cybersecurity for Finance Businesses
In today’s digital age, the finance industry stands as one of the most targeted sectors for cyber attacks. With vast amounts of sensitive data and financial transactions conducted online, the stakes for maintaining robust cybersecurity measures have never been higher. This article explores the critical importance of cybersecurity for finance businesses, the risks they face,…
Continue Reading The Importance of Cybersecurity for Finance Businesses
Why Using AI in Your Business is Easier Than You Think
In recent years, Artificial Intelligence (AI) has transformed from a futuristic concept into a practical tool that businesses of all sizes can leverage. At Dymin, we’ve seen firsthand how AI can revolutionize operations, improve efficiency, and drive innovation. If you’ve been hesitant to integrate AI into your business, let us show you why it’s easier…
Continue Reading Why Using AI in Your Business is Easier Than You Think
The Essential Guide to Firewalls, Switches, and Access Points in Network Security
In the digital age, the importance of robust network security cannot be overstated. For IT professionals and network administrators, safeguarding network infrastructure against cyber threats is a top priority. Among the key players in network defense are firewalls, switches, and access points—each serving a unique yet interconnected role in creating a secure and efficient network.…
Continue Reading The Essential Guide to Firewalls, Switches, and Access Points in Network Security
Unveiling the Power of Co-Managed IT for Mid-Size Businesses
Information Technology (IT) is no longer a back-office operation. Instead, it has become the driving force behind business growth and innovation. For mid-sized businesses, managing the complexities of IT in-house can be arduous and costly, and traditional managed IT services might not always align with their specific needs. This is where Co-Managed IT comes in,…
Continue Reading Unveiling the Power of Co-Managed IT for Mid-Size Businesses
The Ultimate Guide to Cloud Business Phones
In the dynamic landscape of modern business operations, staying connected is not a luxury; it’s a necessity. Small and medium businesses, in particular, constantly seek the most efficient, cost-effective, and scalable solutions to support their growth. With their cumbersome infrastructure and limited features, the once-ubiquitous landline telephones are rapidly fading into obsolescence. Instead, a new…
Continue Reading The Ultimate Guide to Cloud Business Phones
Navigating the Legal Maze of Data Breach Incidents in Business
In our digitally-fused world, the pulsating heart of commerce is no longer just flesh and bone—it’s circuitry, data, and algorithms. Yet, as our businesses evolve to interface almost exclusively through digital channels, a towering menace lurks in the shadows, ready to strike at the bare veins of our operations—data breaches and cyber-attacks. The repercussions of…
Continue Reading Navigating the Legal Maze of Data Breach Incidents in Business
The Essential Role of IT Support in Boosting Success in the Construction Industry
Navigating the modern landscape of the construction industry is a complex endeavor, with its multifaceted projects, stringent timelines, and ever-evolving technology demands. Gone are the days when construction thrived solely on manual labor and on-site expertise. Today, the synergy between Information Technology (IT) and construction is indispensable. At the heart of this synergy lies the…
Continue Reading The Essential Role of IT Support in Boosting Success in the Construction Industry
How to Revolutionize Your Business with Microsoft AI Solutions
In today’s technology-driven business landscape, artificial intelligence (AI) is no longer a distant idea of the future but a pragmatic approach to solving complex problems. Among the leaders in AI solutions is Microsoft, offering a suite of tools that can enhance productivity, boost customer engagement, and streamline operations. But where do you start? The vastness…
Continue Reading How to Revolutionize Your Business with Microsoft AI Solutions
Cloud Migration Essentials: Top Benefits and Effective Strategies for a Smooth Transition
In today’s digital age, the movement of businesses to the cloud is a necessary evolution. Cloud migration offers many advantages, from cost-efficiency to enhanced security, and is a pivotal part of future-proofing enterprises. Yet, the process can be daunting, facing many businesses with tough decisions and complex transitions. This post engages you with invaluable insights…
How Managed IT Protects Dental Clinics From Security Threats
How Managed IT Protects Dental Clinics From Security Threats In the digital age, dental clinics, like all healthcare providers, have become reliant on technology to operate effectively. However, with the increasing sophistication of cyber threats and the importance of patient data security, managing IT internally can quickly overwhelm clinic staff. This is where Managed IT…
Continue Reading How Managed IT Protects Dental Clinics From Security Threats
The Hidden Costs of Cheap IT Solutions for Your Business
In a landscape where technology underpins virtually every aspect of business operations, the lure of cheap IT solutions can be strong. After all, as a business manager or owner, you’re constantly looking for ways to cut costs and maximize budgets. But when it comes to IT, going for the budget options can be a decision…
Continue Reading The Hidden Costs of Cheap IT Solutions for Your Business
Navigating AI’s New Era of Security Threats
In an ever-evolving technological landscape, artificial intelligence (AI) continues to redefine the boundaries of innovation. From enhancing customer experiences with personalized algorithms to automating complex processes, AI has become an integral part of modern business operations. However, as AI systems grow more sophisticated, they concurrently become more vulnerable to security threats. This comprehensive analysis delves…
Continue Reading Navigating AI’s New Era of Security Threats
Empowering Healthcare’s Future With Innovative IT
The heartbeat of healthcare is evolving—keeping pace with technological advancements that not only offer convenience and luxury but also redefine the standards of quality and efficiency. For healthcare professionals and hospital administrators alike, the integration of IT support into the industry’s fabric has become paramount. But why is IT support so crucial in the healthcare…
Continue Reading Empowering Healthcare’s Future With Innovative IT
Know The Truth About Implementing AI For Efficient Business Processes
The hype is real – AI is transforming every industry, promising efficiency, insights, and a competitive edge. But before you jump headfirst into the algorithmic abyss, let’s peel back the curtain and reveal the truth about implementing AI for business processes. 1. Beyond Automation: The Rise of Hyper-personalization: Sure, chatbots can handle FAQs, but the future of…
Continue Reading Know The Truth About Implementing AI For Efficient Business Processes
Why Businesses Should Switch To Cloud Phone Systems In 2024
The emergence of cloud-based phone systems has swiftly taken the business world by storm, garnering attention for their various benefits ranging from cost-effectiveness and versatile features to seamless scalability. One such technology that has become synonymous with modern communications is VoIP (Voice over Internet Protocol). This newer communication system has rapidly gained popularity over the…
Continue Reading Why Businesses Should Switch To Cloud Phone Systems In 2024
How to Practice Quality Cyber Hygiene
In today’s digital age, cyber hygiene is more important than ever. Cyber hygiene refers to the steps that users of computers and other devices can take to improve their online security and maintain system health. It means adopting a security-centric mindset and habits that help individuals and organizations mitigate potential online breaches. A fundamental principle…
7 Reasons Why Avoiding Public Charging Keeps Your Data Safe
In an era dominated by mobile technology, the convenience of public charging for our devices has become a double-edged sword. While it’s tempting to plug in and power up at public charging stations, the potential risks to data security cannot be ignored. In this blog post, we’ll explore seven compelling reasons why avoiding public charging…
Continue Reading 7 Reasons Why Avoiding Public Charging Keeps Your Data Safe
10 Things to Do When Your Computer’s Been Infected
Introduction: Dealing with a computer infection can be a nightmare. Whether it’s a virus, malware, or ransomware, the damage it can cause to your computer and data can be significant. But fear not, because in this guide, we’ll walk you through the ten crucial steps to take when your computer’s been infected. And we’ll also…
Continue Reading 10 Things to Do When Your Computer’s Been Infected
Why Data Recovery Is Important For Your Business
In our increasingly digital world, data is a precious commodity. From personal photos to critical business documents, our lives and livelihoods are often stored electronically. But what happens when that data is suddenly lost or corrupted? That’s where data recovery comes to the rescue. In this comprehensive guide, we’ll explore the world of data recovery,…
Continue Reading Why Data Recovery Is Important For Your Business
10 Comprehensive Benefits of Managed IT Services
In today’s technology-driven world, businesses, regardless of their size, are increasingly reliant on IT infrastructure to operate efficiently. However, managing and maintaining this infrastructure can be a daunting and resource-intensive task. This is where managed IT services come into play, offering a host of benefits that can transform how companies handle their IT needs. In…
Continue Reading 10 Comprehensive Benefits of Managed IT Services
How E-Waste Management Can Save Our Planet
In recent years, there has been a significant increase in electronic waste, or e-waste, contributing to general pollution. This refers to any electronic device or piece of equipment discarded and no longer in use. Everything from computers and cell phones to televisions and refrigerators falls under this category. As technology develops, many electronic items are…
Why Password Managers Are Important? The Best Ones to Use in 2023
In today’s digital age, we all have multiple online accounts. Remembering all the logins can be a real challenge, mainly if we use different accounts’ passwords. This is where password managers come in – they are an essential tool for online security. These tools store all your login credentials in one secure location, usually encrypted…
Continue Reading Why Password Managers Are Important? The Best Ones to Use in 2023
The Importance of Cybersecurity Risk Assessment for Businesses
Risk assessment is an essential process that every business should undertake. Identifying potential hazards and threats that can negatively impact your business is critical. By conducting a risk assessment, you can make informed decisions and take the necessary steps to mitigate risks, ensuring the success of your business. It is an approach that helps organizations…
Continue Reading The Importance of Cybersecurity Risk Assessment for Businesses
5 Benefits of Taking a Digital Detox
In today’s digital landscape, every time it’s more challenging to stay disconnected from technology and devices like social media, email, videogame, tv, and, yes, your smartphone. Technology has made our lives easier in many ways, but it’s important to take a break from it occasionally. A digital detox is a period of time when you…
Protecting Your Privacy: Staying Safe from QR Code Phishing
In today’s digital age, securing your personal information is more critical than ever. One method of cyber attack that has become increasingly prevalent is QR code phishing, also known as quishing. This type of scam involves using QR codes, commonly used to quickly access websites or download apps, to trick people into sharing sensitive information.…
Continue Reading Protecting Your Privacy: Staying Safe from QR Code Phishing
Recycling Solar Panels: Approaching a Greener Future
Solar panels have surged in popularity as a clean and sustainable energy source as the globe increasingly turns to them. However, solar panels have a finite lifespan like any other technology. This raises essential problems about their disposal and potential environmental effects. The advantages of recycling solar panels, the locations where they can be recycled,…
Continue Reading Recycling Solar Panels: Approaching a Greener Future
Why Refurbished Laptops Are a Smart Investment
Do you want to buy a new laptop but want to save money? In that case, you should get a reconditioned laptop. Used laptops that have been brought back to near-new condition are referred to as refurbished laptops. They frequently cost less than brand-new laptops while still having amazing performance and features. Apart from saving…
Continue Reading Why Refurbished Laptops Are a Smart Investment
Benefits of Adopting Cybersecurity Best Practices: HF553
As a small or medium business, cybersecurity best practices should be a big priority. Unfortunately, the vast majority of companies continue to operate under outdated security protocols and are at risk due to the possibility of data breaches or cyberattacks. Even more concerning is House File 553 – proposed legislation that requires businesses to adopt…
Continue Reading Benefits of Adopting Cybersecurity Best Practices: HF553
Common Computer Issues: Troubleshooting Tips and Solutions
From work to recreation, computers have become a necessary part of our daily life. However, they can also be a source of frustration when things go wrong, and even the best computers can experience problems from time to time, so it doesn’t matter if it’s a high-end gaming PC or a regular work laptop if…
Continue Reading Common Computer Issues: Troubleshooting Tips and Solutions
War on Malware: Fortifying Your Business Against Digital Threats
As of today, businesses of all sizes that are involved in digital activity are vulnerable to cyber-attacks and other digital threats. Theft of digital information has surpassed physical theft as the most frequently reported fraud in cybercrime, which is on the rise. The most frequent attack types now include malware, phishing, and ransomware, which can…
Continue Reading War on Malware: Fortifying Your Business Against Digital Threats
Top 5 Graphics Cards for 2023: Get the Most Out of Your Gaming PC
Graphics cards have come a long way in recent years, and the latest models offer incredible performance for gaming, content creation, and other demanding tasks. If you’re looking to upgrade your graphics card in 2023, there are a few things you’ll need to consider before looking at our list of top graphics cards. Performance to…
Continue Reading Top 5 Graphics Cards for 2023: Get the Most Out of Your Gaming PC
The Future of Logistics: Embracing Technology to Stay Ahead
In an ever-evolving world of technology, emerging trends have drastically changed the way logistics and trucking companies operate. Companies that understand these changes and adapt their businesses to stay relevant in this ever-changing landscape will have a distinct advantage over those that don’t. Keeping up with the latest technologies is instrumental for any business hoping…
Continue Reading The Future of Logistics: Embracing Technology to Stay Ahead
Mobile Malware Has Increased 500% – What Should You Do?
Cybersecurity researchers uncovered an alarming mobile statistic. During the first few months of 2022, mobile malware attacks surged by 500%. This is alarming both in scale and because many people aren’t yet protecting smartphones.For years, mobile phones have become more powerful. They now do many of the same functions as a computer – just with…
Continue Reading Mobile Malware Has Increased 500% – What Should You Do?
How Is the Metaverse Going to Change Business?
The new buzzword around town is “metaverse.” But what does that actually mean for businesses? Is it just something that social media companies need to be concerned about?According to people like Apple’s CEO Tim Cook, the metaverse is coming. He stated that “Life without AR will soon be unthinkable.” Whether that’s a short-term or long-off…
Continue Reading How Is the Metaverse Going to Change Business?
Have You Had Data Exposed in a Recent Breach?
There’s a reason that browsers like Edge have added breached password notifications. Data breaches are an unfortunate part of life. And can have costly consequences for individuals. Hackers can steal identities and compromise bank accounts, just to name a couple.Cybercriminals breach about 4,800 websites every month with form jacking code. It has become all too…
Continue Reading Have You Had Data Exposed in a Recent Breach?
2023 Trends in Data Privacy That Impact Your Compliance
Data privacy has been a growing requirement ever since the internet age began. So much personal information is flying around through computer networks. Protecting it has become a mandate.Most companies must follow HIPAA, GDPR, or another industry or locality-based privacy rule. By the end of 2024, 75% of the world’s population will have their personal…
Continue Reading 2023 Trends in Data Privacy That Impact Your Compliance
8 Tech Checks to Make Before You Travel
Our technology inevitably comes with us when we travel. Most of us won’t even travel to the end of the block without our smartphones. When you go on a trip, not having your technology there when you need it can ruin your day.Travel smarter and more securely by doing several checks before you go. Use…
7 Most Exciting App Announcements at Microsoft Ignite 2022
If you follow Microsoft products, then you may know about Microsoft Ignite. Held annually, it generates many exciting updates and announcements in the Microsoft world.Microsoft held its most recent conference last October. In the rush of the recent holidays, you may have missed some of the highlights. So, we’re bringing them to you now.One thing…
Continue Reading 7 Most Exciting App Announcements at Microsoft Ignite 2022
What’s Changing in the Cybersecurity Insurance Market?
Cybersecurity insurance is still a pretty new concept for many SMBs. It was initially introduced in the 1990s to provide coverage for large enterprises. It covered things like data processing errors and online media.Since that time, the policies for this type of liability coverage have changed. Today’s cyber insurance policies cover the typical costs of…
Continue Reading What’s Changing in the Cybersecurity Insurance Market?
Cybersecurity Attack Trends You Should Watch in 2023
The new year has just begun and it’s a time of renewal as we plan for the possibilities to come in 2023. It’s also a time when you need to plan for resiliency in the face of ever-present cyberattacks.Sixty-eight percent of surveyed business leaders feel that cybersecurity risks are getting worse. They have a good…
Continue Reading Cybersecurity Attack Trends You Should Watch in 2023
IT Challenges Facing the Healthcare Industry Today
Managed IT Service Providers facilitate the optimal use of technology in healthcare with security, reliability, and uninterrupted service.
Continue Reading IT Challenges Facing the Healthcare Industry Today
How to Select a Managed Service Provider for Your Business IT Needs
As your business begins transforming digitally, your technology needs will evolve and change. To keep up with chaotic market forces and constant innovations in the digital world, you need to keep integrating new devices, systems, and applications. And yet, to properly upkeep current infrastructure and stay on top of these changes, you need continuous monitoring…
Continue Reading How to Select a Managed Service Provider for Your Business IT Needs
Don’t Set Yourself Up to Fail: Tips for Safer Home Security Setups
The global home security market has been growing by leaps and bounds. By 2026, experts expect the market to expand at a rate of 20.1%. This is on top of an expected increase of 21.6% from 2021 to 2022. From Ring doorbell cams to entire home security systems, consumers want these solutions. Watching your front…
Continue Reading Don’t Set Yourself Up to Fail: Tips for Safer Home Security Setups
Align Your Team to Company Targets with Microsoft Viva Goals
You often hear the words “digital transformation” and “collaboration.” But what do they actually mean? What do they mean for the day-to-day of running your business? Collaboration can’t happen without shared goals. When departments are siloed and unconnected, priorities can conflict. People are doing their best but may not be moving in the same direction.…
Continue Reading Align Your Team to Company Targets with Microsoft Viva Goals
7 VoIP Setup Tips for a More Productive Office
The global pandemic put a big emphasis on the need to run a business from anywhere. Enabling employees to work remotely requires cloud solutions. This includes collaborative platforms like Google Workspace and Microsoft 365. VoIP (Voice over Internet Protocol) phone systems have also become critical. VoIP allows companies to stay in contact with customers and…
Continue Reading 7 VoIP Setup Tips for a More Productive Office
5 Ways to Balance User Productivity with Solid Authentication Protocols
One constant struggle in offices is the balance between productivity and security. If you give users too much freedom in your network, risk increases. But add too many security gates, and productivity can dwindle. It’s a fine balance between the two, but one you can achieve. Organizations need to recognize the importance of both. And…
Continue Reading 5 Ways to Balance User Productivity with Solid Authentication Protocols
What to Include in a Year-end Technology Infrastructure Review
When the year is coming to a close, it’s the perfect time to plan for the future. Most businesses begin the year with the hope of growing and improving operations. Much of how a business operates depends on technology. So, it makes sense to look to your IT for areas of optimization. A year-end technology…
Continue Reading What to Include in a Year-end Technology Infrastructure Review
What Are the Advantages of Implementing Conditional Access?
It seems that nearly as long as passwords have been around, they’ve been a major source of security concern. Eighty-one percent of security incidents happen due to stolen or weak passwords. Additionally, employees continue to neglect the basics of good cyber hygiene. For example, 61% of workers use the same password for multiple platforms. And…
Continue Reading What Are the Advantages of Implementing Conditional Access?
Tips for Overcoming Barriers to a Smooth BYOD Program
Bring your own device (BYOD) is a concept that took hold after the invention of the smartphone. When phones got smarter, software developers began creating apps for those phones. Over time, mobile device use has overtaken desktop use at work. According to Microsoft, mobile devices make up about 60% of the endpoints in a company…
Continue Reading Tips for Overcoming Barriers to a Smooth BYOD Program
Simple Setup Checklist for Microsoft Teams
Microsoft Teams is a lot of things. It’s a video conferencing tool, a team messaging channel, and a tool for in-app co-authoring, just to name a few. During the pandemic, the popularity of Teams skyrocketed. User numbers for MS Teams jumped from 20 million in November 2019 to 75 million in April 2020. As of…
7 Things to Consider When Getting a New Computer to Avoid Buyer’s Remorse
Have you ever bought a new computer and then had buyer’s remorse a few months later? Maybe you didn’t pay attention to the storage capacity and ran out of space. Or you may have glossed over memory and experienced constant freeze-ups. An investment in a new PC isn’t something you want to do lightly. Doing…
Continue Reading 7 Things to Consider When Getting a New Computer to Avoid Buyer’s Remorse
7 Apps That Can Help You Improve Customer Experience in 2023
Paying attention to your customer experience directly impacts your bottom line. Companies that are “customer-centric” are 60% more profitable than those that aren’t. In this digital age, customers also expect more from those they do business with. In today’s world, people can order something on their phones and see it on their doorstep the next…
Continue Reading 7 Apps That Can Help You Improve Customer Experience in 2023
What Are the Most Helpful VoIP Features for Small Businesses?
Just five or six years ago, VoIP was still considered a “different” type of business phone system. One that wasn’t the norm. But the pandemic changed that way of thinking. Now internet-based phone systems aren’t simply the norm. They’re mandatory for business continuity. During the pandemic, VoIP and video conferencing have skyrocketed by over 210%.…
Continue Reading What Are the Most Helpful VoIP Features for Small Businesses?
Simple Guide to Follow for Better Endpoint Protection
Endpoints make up much of a company’s network and IT infrastructure. This is a collection of computers, mobile devices, servers, and smart gadgets. As well as other IoT devices that all connect to the company network. The number of endpoints a company has will vary by business size. Companies with less than 50 employees have…
Continue Reading Simple Guide to Follow for Better Endpoint Protection
Insider Threats Are Getting More Dangerous! Here’s How to Stop Them
One of the most difficult types of attacks to detect are those performed by insiders. An “insider” would be anyone that has legitimate access to your company network and data. This would be via a login or other authorized connection. Because insiders have authorized system access, they bypass certain security defenses. Such as those designed…
Continue Reading Insider Threats Are Getting More Dangerous! Here’s How to Stop Them
Everything You Need to Know About Microsoft Viva Sales
Data entry can be a real drag for salespeople. The time they spend on administrative tasks is time away from customer interactions. But that data is vital. It’s important to capture customer orders, quotes, needs, and more. Lead and sales reporting help sales managers know where to direct their attention. Analytics also help drive more…
Continue Reading Everything You Need to Know About Microsoft Viva Sales
Checklist for Better Digital Offboarding of Employees
Digital footprints cover today’s modern workplace. Employees begin making these the moment they’re hired. They get a company email address and application logins. They may even update their LinkedIn page to connect to your company. When an employee leaves a company, there is a process that needs to happen. This is the process of “decoupling”…
Continue Reading Checklist for Better Digital Offboarding of Employees
9 Urgent Security Tips for Online Holiday Shopping
The holiday shopping season is taking off. This means that scammers have also revved up their engines. They’re primed and ready to take advantage of all those online transactions. Don’t forget to stay safe online during the buying frenzy that occurs this time of year. An ounce of cybersecurity prevention is definitely worth a pound…
Continue Reading 9 Urgent Security Tips for Online Holiday Shopping
7 Pro Tips for Microsoft 365
Microsoft 365 is the most popular of all major office productivity software. It has 48.8% of the global market share, just edging out Google’s apps, by a couple of percentage points. It’s used by individuals, small & mid-sized businesses, and larger enterprise organizations. It does everything a modern office needs. Including from word processing and…
What Is Microsoft Defender for Individuals & What Does It Do?
When you hear about Microsoft adding security apps to M365, it’s often the business versions. But the pandemic has changed the way that we see the workplace. It’s now a hybrid world. One made up of several connected “mini-offices” located in employee homes. The outsourcing market has also contributed to the change in company networks.…
Continue Reading What Is Microsoft Defender for Individuals & What Does It Do?
The Biggest Vulnerabilities that Hackers are Feasting on Right Now
Software vulnerabilities are an unfortunate part of working with technology. A developer puts out a software release with millions of lines of code. Then, hackers look for loopholes that allow them to breach a system through that code. The developer issues a patch to fix the vulnerability. But it’s not long before a new feature…
Continue Reading The Biggest Vulnerabilities that Hackers are Feasting on Right Now
Small Businesses Are Attacked by Hackers 3x More than Larger Ones
Have you felt more secure from cyberattacks because you have a smaller business? Maybe you thought that you couldn’t possibly have anything that a hacker could want? Didn’t think they even knew about your small business. Well, a new report by cybersecurity firm Barracuda Networks debunks this myth. Their report analyzed millions of emails across…
Continue Reading Small Businesses Are Attacked by Hackers 3x More than Larger Ones
Internet Explorer Has Lost All Support (What You Need to Know)
After being the main entry to the internet in the late 1990s and early 2000s, Internet Explorer (IE) is gone. As of June 15, 2022, Microsoft dropped the web browser from support. IE ushered in the age of connection to the world in 1995 and held a majority of the browser market share for many…
Continue Reading Internet Explorer Has Lost All Support (What You Need to Know)
5 Mistakes Companies Are Making in the Digital Workplace
The pandemic has been a reality that companies around the world have shared. It required major changes in how they operate. No longer, did the status quo of having everyone work in the office make sense for everyone. Many organizations had to quickly evolve to working through remote means. During the worst of the pandemic,…
Continue Reading 5 Mistakes Companies Are Making in the Digital Workplace
You Need to Watch Out for Reply-Chain Phishing Attacks
Phishing. It seems you can’t read an article on cybersecurity without it coming up. That’s because phishing is still the number one delivery vehicle for cyberattacks. A cybercriminal may want to steal employee login credentials. Or wish to launch a ransomware attack for a payout. Or possibly plant spyware to steal sensitive info. Sending a…
Continue Reading You Need to Watch Out for Reply-Chain Phishing Attacks
What Should You Do to Reduce Risk When Your Mobile Device Goes Missing?
Few things invoke instant panic like a missing smartphone or laptop. These devices hold a good part of our lives. This includes files, personal financials, apps, passwords, pictures, videos, and so much more. The information they hold is more personal than even that which is in your wallet. It’s because of all your digital footprints.…
Continue Reading What Should You Do to Reduce Risk When Your Mobile Device Goes Missing?
Microsoft Productivity Score Overview
Productivity can be challenging to track, no matter where employees are working. How do you know they’re using their tools as effectively as possible? How can you enable them to adopt best practices? These are questions that managers often ask themselves. If they’re looking at the wrong things, it can get in the way of…
Helpful Tips for Keeping Your Shared Cloud Storage Organized
Cloud file storage revolutionized the way we handle documents. No more having to email files back and forth. No more wondering which person in the office has the most recent copy of a document. Between 2015 and 2022, the percentage of worldwide corporate data stored in the cloud doubled. It went from 30% to 60%.…
Continue Reading Helpful Tips for Keeping Your Shared Cloud Storage Organized
6 Important IT Policies Any Size Company Should Implement
Many small businesses make the mistake of skipping policies. They feel that things don’t need to be so formal. They’ll just tell staff what’s expected when it comes up and think that’s good enough. But this way of thinking can cause issues for small and mid-sized business owners. Employees aren’t mind readers. Things that you…
Continue Reading 6 Important IT Policies Any Size Company Should Implement
6 Discontinued Technology Tools You Should Not Be Using Any Longer
One constant about technology is that it changes rapidly. Tools that were once staples, like Internet Explorer and Adobe Flash, age out. New tools replace those that are obsolete. Discontinued technology can leave computers and networks vulnerable to attacks. While older technology may still run fine on your systems that doesn’t mean that it’s okay…
Continue Reading 6 Discontinued Technology Tools You Should Not Be Using Any Longer
How Using the SLAM Method Can Improve Phishing Detection
There is a reason why phishing is usually at the top of the list for security awareness training. For the last decade or two, it has been the main delivery method for all types of attacks. Ransomware, credential theft, database breaches, and more launch via a phishing email. Why has phishing remained such a large…
Continue Reading How Using the SLAM Method Can Improve Phishing Detection
Did You Receive a Text from Yourself? It’s Probably Smishing
How many text messages from companies do you receive today as compared to about two years ago? If you’re like many people, it’s quite a few more. This is because retailers have begun bypassing bloated email inboxes. They are urging consumers to sign up for SMS alerts for shipment tracking and sale notices. The medical…
Continue Reading Did You Receive a Text from Yourself? It’s Probably Smishing
How Often Do You Need to Train Employees on Cybersecurity Awareness?
You’ve completed your annual phishing training. This includes teaching employees how to spot phishing emails. You’re feeling good about it. That is until about 5-6 months later. Your company suffers a costly ransomware infection due to a click on a phishing link. You wonder why you seem to need to train on the same information…
Continue Reading How Often Do You Need to Train Employees on Cybersecurity Awareness?
Home Security: Why You Should Put IoT Devices on a Guest Wi-Fi Network
The number of internet-connected devices in homes has been growing. It’s increased exponentially over the last decade. A typical home now has 10.37 devices connected to the internet. PCs and mobile devices make up a little over half of those and the rest are IoT devices. IoT stands for Internet of Things. It means any…
Continue Reading Home Security: Why You Should Put IoT Devices on a Guest Wi-Fi Network
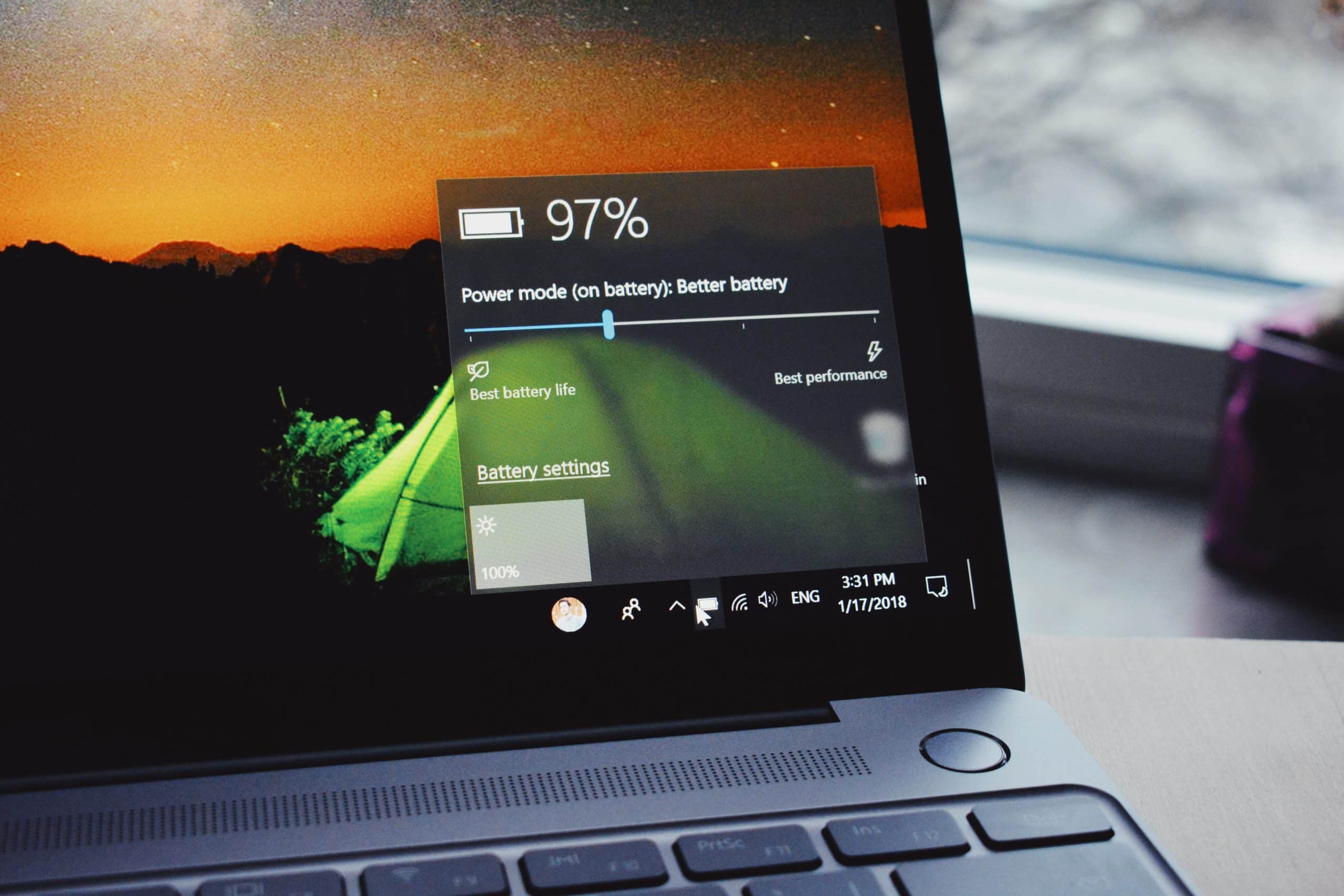
Get More Unplugged Laptop Time with These Battery-Saving Hacks
One of the big draws of a laptop computer is that you can use it anywhere. You don’t need to have it plugged in all the time because it has an internal battery. Your laptop may start out with several hours of battery life when you first buy it. But the lifespan can get shorter…
Continue Reading Get More Unplugged Laptop Time with These Battery-Saving Hacks
5 Exciting Ways Microsoft 365 Can Enable the Hybrid Office
“Hybrid office” is the new buzzword you’ll hear used in business discussions. It’s the mix of having employees both working at the office and working from home. This has become more than a buzzword and is now the reality for many companies. There was a survey of employees with remote-capable jobs. The survey found that…
Continue Reading 5 Exciting Ways Microsoft 365 Can Enable the Hybrid Office
Which Form of MFA Is the Most Secure? Which Is the Most Convenient?
Credential theft is now at an all-time high and is responsible for more data breaches than any other type of attack. With data and business processes now largely cloud-based, a user’s password is the quickest and easiest way to conduct many different types of dangerous activities. Being logged in as a user (especially if they…
Continue Reading Which Form of MFA Is the Most Secure? Which Is the Most Convenient?
Top 5 Mobile Device Attacks You Need to Watch Out For
Smartphones and tablets are often the preferred device for communications, web searching, and accessing many types of apps. They’re more portable and can be used from anywhere. We’re seeing the takeover of many activities that used to be performed on traditional computers. Now, people are using mobile devices instead. For example, Microsoft estimates that up…
Continue Reading Top 5 Mobile Device Attacks You Need to Watch Out For
Signs That Your Computer May Be Infected with Malware
Approximately 34% of businesses take a week or longer to regain access to their data and systems once hit with a malware attack. Malware is an umbrella term that encompasses many different types of malicious code. It can include: Viruses Ransomware Spyware Trojans Adware Key loggers And more The longer that malware sits on your…
Continue Reading Signs That Your Computer May Be Infected with Malware
Should I Consider Switching to Microsoft’s Edge Browser? (Top Features)
One of the most important applications we choose is our internet browser. When on a computer or a mobile device, we work in that most of the time because many applications are now cloud-based, so accessing them means going through your browser. Over the years browsers have come and gone. A little over a decade…
Continue Reading Should I Consider Switching to Microsoft’s Edge Browser? (Top Features)
Pros & Cons of Using the Windows 365 Cloud PC
While many companies have moved most of their workflows to the cloud, there is still a key component of office operations that is location-based. This would be employee computers. Most companies still rely on desktops and laptops to allow employees to access critical software and as their main workstation. This can become inconvenient if you’re…
Continue Reading Pros & Cons of Using the Windows 365 Cloud PC
Are Two Monitors Really More Productive Than One?
When you see those people with two monitors, you may assume they do some specialized work that requires all that screen space, or they just really like technology. But having the additional display real estate that a second screen provides can benefit anyone, even if you’re doing accounting or document work all day. We get…
Continue Reading Are Two Monitors Really More Productive Than One?
What You Need to Know About the Rise in Supply Chain Cyberattacks
Any cyberattack is dangerous, but the particularly devastating ones are those on supply chain companies. These can be any supplier – digital or non-digital – of goods and services. We’ve seen several attacks on the supply chain occur in 2021 that had wide-reaching consequences. These are “one-to-many” attacks where victims can go far beyond the…
Continue Reading What You Need to Know About the Rise in Supply Chain Cyberattacks
What Are the Best Ways to Give an Older PC New Life?
Purchasing a new computer is a big investment. Many small businesses and home PC owners end up struggling with older systems because they want to get as many years out of them as possible. Have you found yourself banging on your keyboard in frustration? Have you tried every tip and trick you found online, only…
Continue Reading What Are the Best Ways to Give an Older PC New Life?
Microsoft Teams Plans: Free vs M365 Business vs Teams Essentials
The shift to remote work over the last two years has caused companies to realign their digital tools. Now, many meetings default to being via video conference rather than in person, and working from home has become commonplace. Seventy-seven percent of remote workers say they’re more productive working from home (a big reason is fewer…
Continue Reading Microsoft Teams Plans: Free vs M365 Business vs Teams Essentials
Dymin Systems Ranked Top Third on Channel Futures 2022 MSP 501
Dymin Systems Ranked Top Third on Channel Futures 2022 MSP 501—Tech Industry’s Most Prestigious List of Managed Service Providers Worldwide
Continue Reading Dymin Systems Ranked Top Third on Channel Futures 2022 MSP 501